The price of Bitcoin suffered a fatal setback last week as it revisited the crash levels of May 19, but this week is promising.Miners scramble to reallocate as China crackdown on BTC mining in several regions.Investors are mobilizing to offset Bitcoin's energy consumption through green initiatives.Bitcoin's price action has been brutal over the past week as it slipped to … [Read more...] about Miners Face Metaphorical Ax As Investors Push For Green BTC
Uncategorized
MIT explains why internet users are sharing fake news
Internet users rarely seek to deceive and we are rather dealing with inattention and a lack of knowledge.It has widely commented online disinformation on in recent years and in particular the deleterious effects it can produce in terms of democratic life, or in the fight against climate change. The giants of the web are often blamed, and, despite their efforts, they often … [Read more...] about MIT explains why internet users are sharing fake news
You can’t install Windows 11 on Mac without this trick
Microsoft unveiled a certain Windows 11 last Thursday, the next major update to its PC operating system. While it comes with an updated design and even the ability to run emulated Android apps, not everyone will install the new version. In fact, any Intel Mac will not officially support Windows. Even less on the Mac M1.We know Windows to run on most machines on the market, … [Read more...] about You can’t install Windows 11 on Mac without this trick
Black day for Bitcoin mining, weighed down by China
It's the crisis for BTC mining equipment manufacturers. The manufacturer Bitmain suspends sales of machines, the prices of which are plummeting.The ban on Bitcoin mining in China has serious repercussions. The effects are felt beyond the single price of BTC, subject to strong tensions. During the week, the price of Bitcoin dropped back below $30,000.But it is also … [Read more...] about Black day for Bitcoin mining, weighed down by China
Android: Joker malware threatens to steal your money, quickly uninstall these 8 apps!
The Joker malware is once again back. Hidden in the code of 8 apps from the Google Play Store, the malware seeks to collect user data. Above all, it threatens to steal money from its victims by subscribing them to online services that are as unnecessary as they are expensive. Here is the list of infected applications to urgently uninstall from your smartphone. In a report … [Read more...] about Android: Joker malware threatens to steal your money, quickly uninstall these 8 apps!
Designer imagines video for original Macintosh
Apple has been making great videos to unveil its novelties on stage since last year, but that hasn't always been the case. Because of the limitations of technology, products like the original Macintosh never had a super 3D introduction - although the “1984” ad is pretty iconic. Now Thibaut Crepelle has created a video to show what the introduction of the Macintosh would look … [Read more...] about Designer imagines video for original Macintosh
This billionaire “converted to crypto” who does not want to “miss” the crypto turn!
Crypto investors are pretty much on the run right now! Indeed, after a relatively calm week, crypto prices seem to gogo down again this week. However, a billionaire investor has just declaimed his attachment to cryptos... What to restore balm to the hearts of crypto investors?Steve Cohen, a billionaire “converted” to cryptocurrencies!Steve Cohen is not necessarily one … [Read more...] about This billionaire “converted to crypto” who does not want to “miss” the crypto turn!
Faulty facial recognition in the United States prevents job seekers from touching their unemployment
To combat unemployment benefit fraud, many American states have used the “ID.me” service employing facial recognition. But serious dysfunctions would simply prevent thousands of beneficiaries from having access to it.Denounced for many months in no less than 24 American states, in particular on the social network Twitter, these blocks do not seem to be lifted, while the CEO … [Read more...] about Faulty facial recognition in the United States prevents job seekers from touching their unemployment
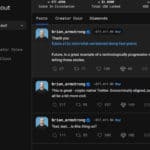
Cryptocurrency: This Controversial Site Gives People A Price
The mysterious platform, which hides the name of its creator, is halfway between a social network and a stock exchange. The performance and influence of people in society is at stake.In a tweet, Coinbase CEO Brian Armstrong fueled a controversy that is far from abating. “I just configured my bitclout,” he wrote on the media, referring to a platform halfway … [Read more...] about Cryptocurrency: This Controversial Site Gives People A Price
iPhone: this magic trick will amaze all your friends
Want to impress your friends with a magic trick? Your best ally will be… their iPhone! In a few clicks and with a well-established demonstration, you will impress your audience. We explain to you.How to impress your audience with a magic trick without a card, a dove, or a hat? With an iPhone, of course! We give you a little trick that relies on the memory of the … [Read more...] about iPhone: this magic trick will amaze all your friends