There are two ways to “win”: to be better than the other or to make the other less. While most people are honest and believe in the virtues of hard work and discipline, unfortunately not everyone.Negative SEO is a set of bad SEO practices performed by a third party to intentionally lower your rank on search engines and harm your visibility.How to spot a negative SEO … [Read more...] about Negative SEO: what to do?
How to Develop B2B Sales Processes to Meet the Requirements of Modern Decision-Makers?
It's no secret that B2B selling has always been difficult. But it may be even more so today. Salespeople feel they no longer have control over the sales process. As studies show, B2B buyers increasingly prefer to research and select products themselves, without being influenced by a seller:Only 29% of buyers want to speak to a seller to learn more about the … [Read more...] about How to Develop B2B Sales Processes to Meet the Requirements of Modern Decision-Makers?
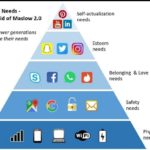
Maslow’s pyramid of needs applied to digital marketing
Maslow's Pyramid is a marketing classic, but do you know what it means? Today we take you through what it is and how to use this theory in your online marketing strategy. The idea is to help you get to know your target audience better to differentiate yourself, segment well, and better plan your content.Today, I am collaborating on the blog to tell you about the Maslow … [Read more...] about Maslow’s pyramid of needs applied to digital marketing
Create A/B tests with Google Optimize to improve conversion
Google Optimize is a free Google Analytics 360 testing platform, with which you can create experiments and A / B tests, to improve the conversion rate [CRO] of your website.Optimization is directly linked to conversion. Google Optimize is the perfect platform to test different versions of your website elements and designs and, based on the results, design your website to … [Read more...] about Create A/B tests with Google Optimize to improve conversion
How to decrease the bounce rate of your site?
The bounce rate is the percentage of users who have visited only one page on your site. In other words, it is the ratio of visitors who left your site after viewing only one page.The time dimension has no impact on the bounce rate. Whether the visits last 4 seconds or 45 minutes, they will count towards the bounce rate if the visitor leaves your site after … [Read more...] about How to decrease the bounce rate of your site?
How to optimize your images for the web in 3 steps?
With the proliferation of interfaces and internet connections, the performance of a website and page load time are becoming increasingly important issues. Whether it is improving the user experience or optimizing your natural referencing, managing your image files is a lever to work with rigorously. We are going to answer together with the question that many … [Read more...] about How to optimize your images for the web in 3 steps?
What is internal mesh and how to set it up?
If we know the importance of links and net linking in SEO, we tend to underestimate the power of a good “on-site” SEO strategy. However, effective internal linking can considerably improve its performance and its positioning in search engines. So, why optimize your internal linking? And how to.If we know the importance of links and net linking in SEO, we tend to … [Read more...] about What is internal mesh and how to set it up?
Online reputation: the key to success in 2021
Often neglected by companies starting their digital transformation, e-reputation is nevertheless an important driver of growth. This is even more true in our time when the border between e-reputation and the overall brand image of the company tends to disappear completely! But what is the real impact of online reputation on a company's activity? And how can you master it? We … [Read more...] about Online reputation: the key to success in 2021
Why is paid SEO becoming a must? Google ads
Being referenced on the first page of search engines is a crucial issue for converting via your website: 91% of Internet users click on a link positioned on the first page of results. You know what you have to do if you want to increase awareness and conversion of your business website.Consumers are increasingly connected, whether on tablets, computers, or smartphones. … [Read more...] about Why is paid SEO becoming a must? Google ads
How to establish a winning business prospecting plan?
Because you will very rarely be asked to sell less (except to shift sales to the next month) because you are not the only ones on the market and consumers are more and more chi, demanding and connected, today you must show patience and determination to get an appointment with a prospect of interest to your company. Prospecting has become an art form where some excel and others … [Read more...] about How to establish a winning business prospecting plan?