The FBI will dump the collections of compromised passwords it uncovers in its investigations into Pwned Password, the section of Have I Been Pwned dedicated to passwords. Good news for data breach victims.
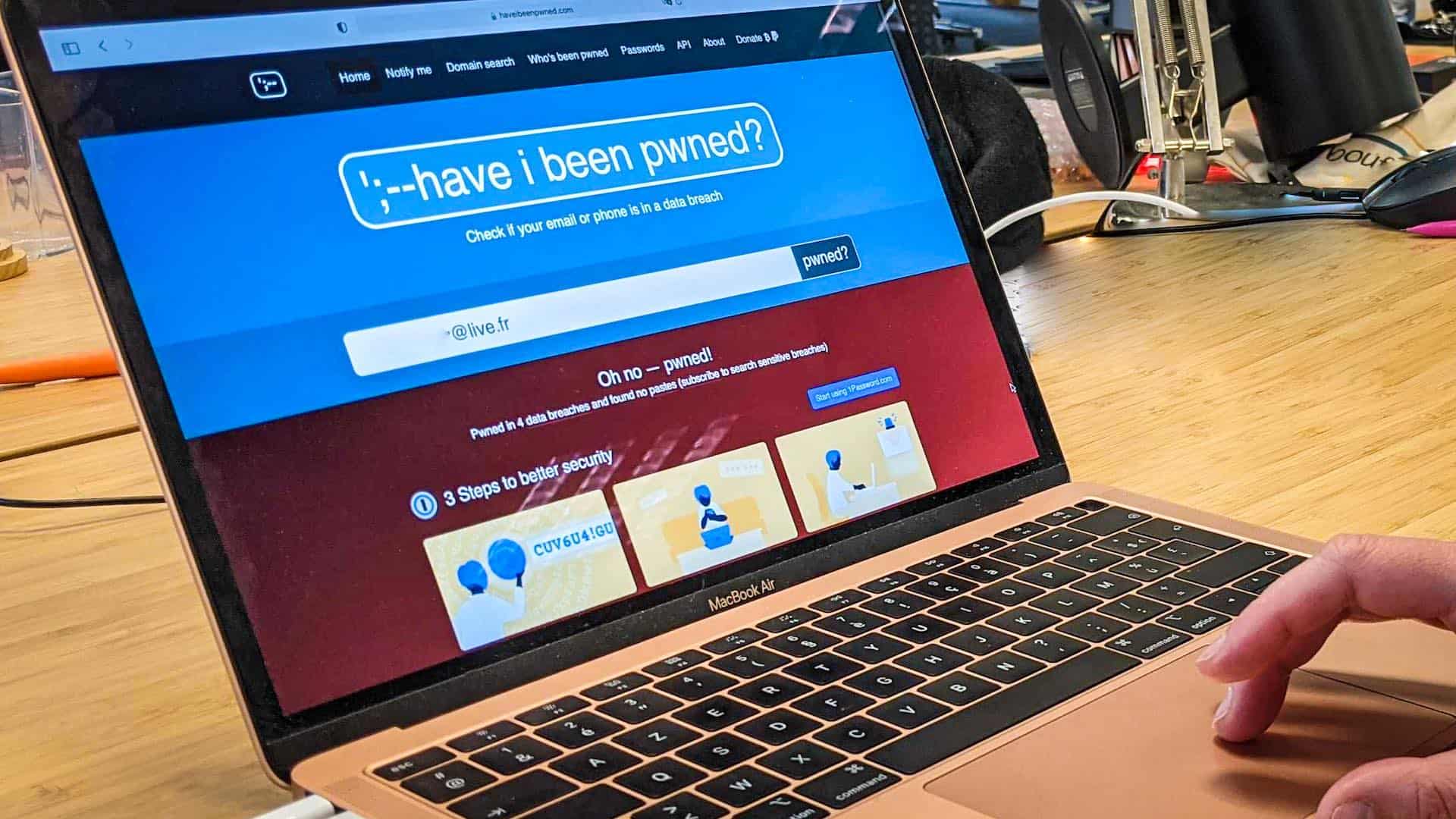
Last month, the FBI for the first time shared data from the victims of one of its investigations – that of the Emotet gang – with the Have I Been Pwned (HIBP) site. Gigantic collection point for data leaks, this site has an exceptional place in the cybersecurity ecosystem: it allows millions of Internet users to know for free when their email address or their password has been leaked.
As an unofficial reward for its services, HIBP has enjoyed impunity since its creation in 2013. It is not worried about its collection of data leaks, a practice which is however difficult to comply with certain regulations such as the GDPR. While it flirts with the limits of the law, the site fills a void left by this same right in the life of personal data after their leak. In the end, the public authorities are thrilled to rely on Have I Been Pwned as a trusted partner. Starting with the FBI: sharing Emotet’s data has been a successful trial run.

Troy Hunt, the founder of HIBP, announced on his blog on May 28 that now, when the FBI finds a collection of passwords in its investigations, it can dump them on Pwned Password, the dedicated Have I Been Pwned tab. passwords. According to Hunt, this feature receives nearly a billion requests per month, proof of its success.
Hash Passwords For Added Security
The investigation office thus becomes the first official contributor to Have I Been Pwned, which has relied since its creation on ad hoc submissions from various sources, sometimes anonymous. Specifically, the FBI will give the site only passwords, and no other information. They will be “hashed” protected by an encryption (SHA-1 or NTLM). For example, the hash of the password “12345” in SHA-1 becomes “8cb2237d0679ca88db6464eac60da96345513964”. Of course, HIBP users will not have to know their password hash, it is the site that will apply the encryption to do its research. Troy Hunt or a hacker of the site cannot read the passwords in the clear, but the encryption will not prevent the proper functioning of the site.
17 Governments Use Pwned Password
Pwned Password passwords can be downloaded or called up through an API, and they are built into all kinds of tools. This operation means that the FBI will make public the hashes of the passwords of the victims of its investigations. Be aware that decrypting hashes is a laborious task for complex passwords, but relatively easy to do for simple passwords. Overall, they expected the initiative to help thousands of people avoid hacks. For example, 17 governments are using the service to make sure their employees are not using already leaked passwords.
Knowing that they have leaked your password is very important. When hackers discover a password, they add it to lists that they will use to connect to all kinds of accounts: social networks, SVoD, but also addresses and professional tools. If the victim reuses their password on several accounts, they will lose control of them.
Pwned Password Is Also Becoming Open Source
Troy Hunt took advantage of his blog to make another announcement, that of the opening of Pwned Password in open source, a project he has been thinking about since August 2020. Concretely, the code of his tool is available on GitHub and developers in all genres can offer their contribution.
The interest of this approach is threefold:
- It perpetuates the project. Today, Have I Been Pwned entirely depends on Troy Hunt, and if it were to suddenly disappear, the site would disappear with him.
- This is an important proof of transparency. In open source, anyone can check their tool, make sure that it is not vulnerable, or that Hunt is not lying about how it works.It allows to consider a real development of the tool.
- Hunt asked them. NET Foundation to oversee the contributions and manage the community. He can suggest the development of new functionalities, as well as receive new suggestions for evolution.
